Conveyor (Automata Network)
 Conveyor - The Automata Network approach to tackling MEV
Conveyor - The Automata Network approach to tackling MEV
At Automata, we have created Conveyor, a service that ingests and outputs transactions in a determined order. This creates a front-running-free zone that removes the chaos of transaction reordering.
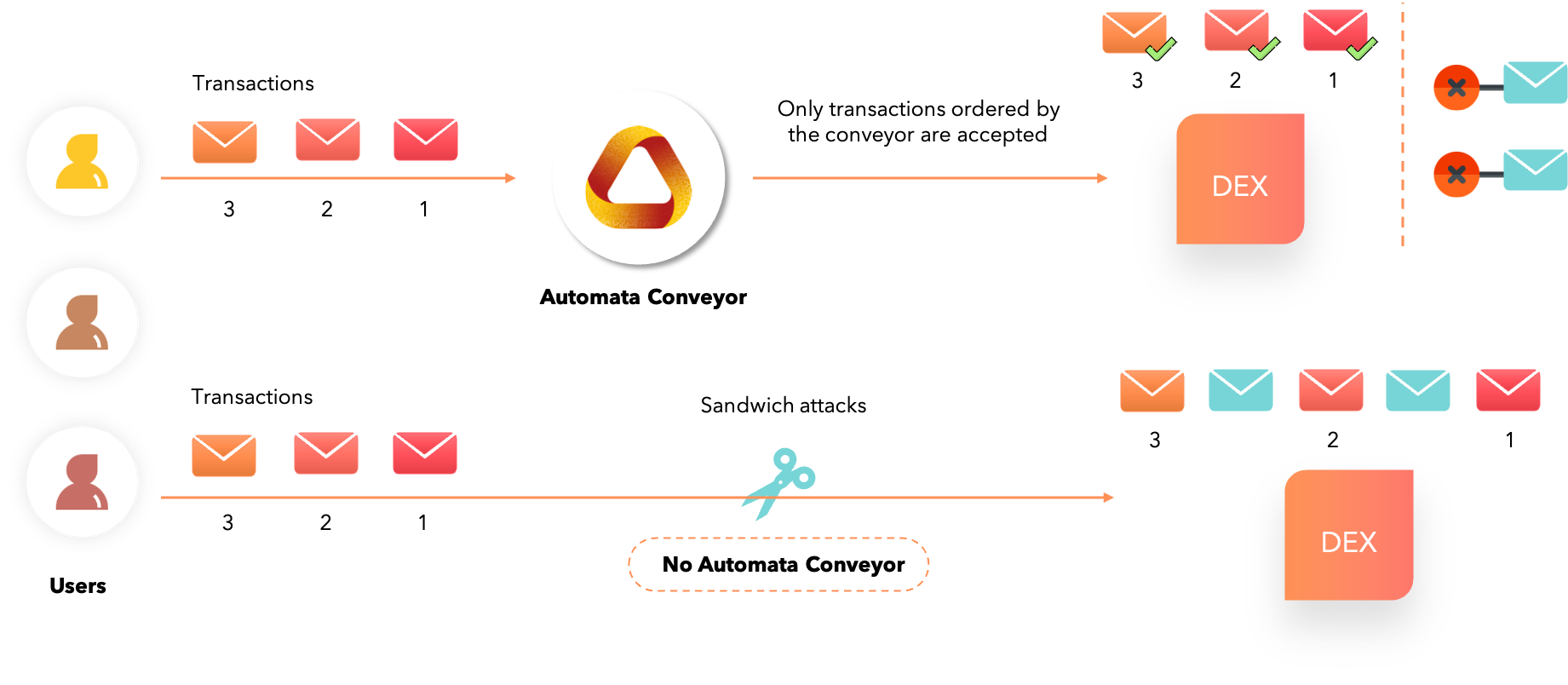
When transactions are fed into Conveyor, it determines the order of the incoming transactions and makes it impossible for block producers to perform the following:
- Inject new transactions into the Conveyor output: The inserted transactions bypassing Conveyor is detectable by anyone because of signature mismatch.
- Delete ordered transactions: Transactions accepted by Conveyor are broadcasted everywhere so transactions cannot be deleted unless ALL block producers are colluding and censoring the transactions at the same time.
From the DEX’s perspective, they can choose to accept either
- Ordered transactions from Automata’s Conveyor which is free from transaction reordering and other front-running transactions
- Other unordered transactions (which include front-running etc) that may negatively impact their users
Why should users trust Conveyor?
Automata’s Conveyor runs on a decentralized compute plane backed by many Geode instances. Each Geode instance can be attested so anyone can publicly verify that the Geode is running on a system with genuine hardware (i.e., CPU) and that the Geode application code matches the version that is open-sourced and audited. This provides a strong guarantee that:
- The Geode code is untampered with
- The Geode data is inaccessible to even Geode providers (In which case they cannot act on said data to front-run transactions)
Importantly, Automata’s Conveyor is a chain-agnostic solution to the MEV issue, and works seamlessly on various platforms — zero modifications needed.
An industry-first: Oblivious RAM
In fully public computation, access pattern leakage is not negligible as everything is exposed. But in privacy-preserving computation, any tiny bit of information leakage becomes a significant issue. Studies have shown that access pattern leakage leads to exposure of sensitive information such as private keys from searchable encryption and trusted computing.
This is where the Oblivious RAM algorithm comes into play. Automata’s implementation is the first-of-its-kind in the blockchain industry, providing an exceedingly high degree of privacy in dApps.
This greatly reduces the probability of user privacy being leaked even as access patterns are being monitored and analyzed by malicious actors. The Automata team has authored multiple research papers on state-of-the-art ORAM and hardware technologies to enhance the privacy and performance of existing networks.
- Robust P2P Primitives Using SGX Enclaves RAID 2020
- PRO-ORAM: Practical Read-Only Oblivious RAM RAID 2019
- OblivP2P: An Oblivious Peer-to-Peer Content Sharing System USENIX Security 2016
- Preventing Page Faults from Telling Your Secrets Asia CCS 2016
Official Links
Website: https://ata.network/
Whitepaper: https://xata.to/lightpaper
GitHub: https://xata.to/github
Documentation: https://docs.ata.network/
Ambassador program form: https://xata.to/ambassadors
FAQ: https://xata.to/faq
Official Socials
Telegram Annoucement Channel: https://t.me/ata_announcement
Telegram Chat Group: https://xata.to/telegram
Twitter: https://xata.to/twitter
Discord: https://xata.to/discord
Medium: https://xata.to/medium
Community Links
Korea (Telegram): https://t.me/atanetworkkorea
Spain (Telegram): https://t.me/atanetworkspanish
Sri Lanka (Telegram): https://t.me/atanetworksinhala
Russian (Telegram): https://t.me/atanetworkrussia
Malay-Indonesian (Telegram): https://t.me/atanetworkmalaysia
Other useful links
MEV Checkup Tool: https://mev.tax/
Coinmarketcap article: https://xata.to/vxa
Binance research report: https://xata.to/br
Binance launchpool annoucement: https://xata.to/186e34